SSH To Raspberry Pi Behind Firewall Without MAC On Windows: The Ultimate Guide
Ever found yourself scratching your head trying to connect to your Raspberry Pi behind a firewall without knowing its MAC address? Don’t worry—you’re not alone. SSH to Raspberry Pi behind firewall without MAC Windows is a common challenge faced by many enthusiasts and professionals alike. In this article, we’ll break it down step by step, making sure even beginners can follow along.
Whether you’re a tech-savvy hobbyist or just starting out with Raspberry Pi, setting up SSH connections can sometimes feel like navigating a maze. But fear not! By the end of this guide, you’ll have all the tools and knowledge needed to remotely access your Pi, even when it’s tucked behind a firewall.
This isn’t just about solving a technical problem—it’s about empowering you to take control of your projects. So grab your favorite beverage, settle into your favorite chair, and let’s dive deep into the world of SSH and Raspberry Pi magic!
- Juan Pablo Di Pace Wife The Untold Story You Need To Know
- Decorating With Kda Designology Transform Your Space Into A Masterpiece
Understanding SSH and Its Importance in Raspberry Pi Projects
SSH, or Secure Shell, is like the secret handshake that lets you securely communicate with your Raspberry Pi from anywhere. It’s a protocol designed to provide encrypted communication between devices, ensuring your data stays safe even if someone tries to eavesdrop. When you’re working on projects that require remote access, SSH becomes an indispensable tool.
For Raspberry Pi users, SSH offers a way to manage files, run commands, and monitor processes without needing physical access to the device. This is especially useful if your Pi is set up in a remote location or behind a network firewall. By mastering SSH, you unlock the full potential of your Pi, turning it into a powerful server, media center, or IoT hub.
Why SSH Matters for Raspberry Pi Behind Firewalls
Firewalls are great for security, but they can also block incoming connections, making it tricky to SSH into your Pi. That’s why understanding how SSH works within this context is crucial. Here’s why SSH matters:
- Remove Clothes Ai Free The Ultimate Guide To Exploring And Understanding
- Annamalai Family Photos A Heartwarming Journey Through Time And Tradition
- Secure Communication: SSH encrypts all data exchanged between your computer and the Pi, preventing unauthorized access.
- Remote Control: With SSH, you can control your Pi as if you were sitting right in front of it, no matter where you are.
- Efficiency: SSH eliminates the need for physical interaction, saving time and effort in managing your projects.
Now that we’ve covered the basics, let’s move on to the specifics of setting up SSH when your Pi is behind a firewall.
Setting Up SSH on Raspberry Pi: Step-by-Step Guide
Before diving into the complexities of firewalls, let’s ensure your Raspberry Pi is properly configured for SSH. Follow these steps to get everything up and running:
Step 1: Enable SSH on Your Raspberry Pi
- Insert your Raspberry Pi SD card into your computer.
- Open the boot partition and create a new file named
ssh(no extension). - Insert the SD card back into your Pi and power it on. SSH should now be enabled.
Step 2: Find Your Pi’s IP Address
- Use a network scanner tool like Advanced IP Scanner or Angry IP Scanner to locate your Pi’s IP address.
- Alternatively, log into your router’s admin panel and look for the device list to find your Pi.
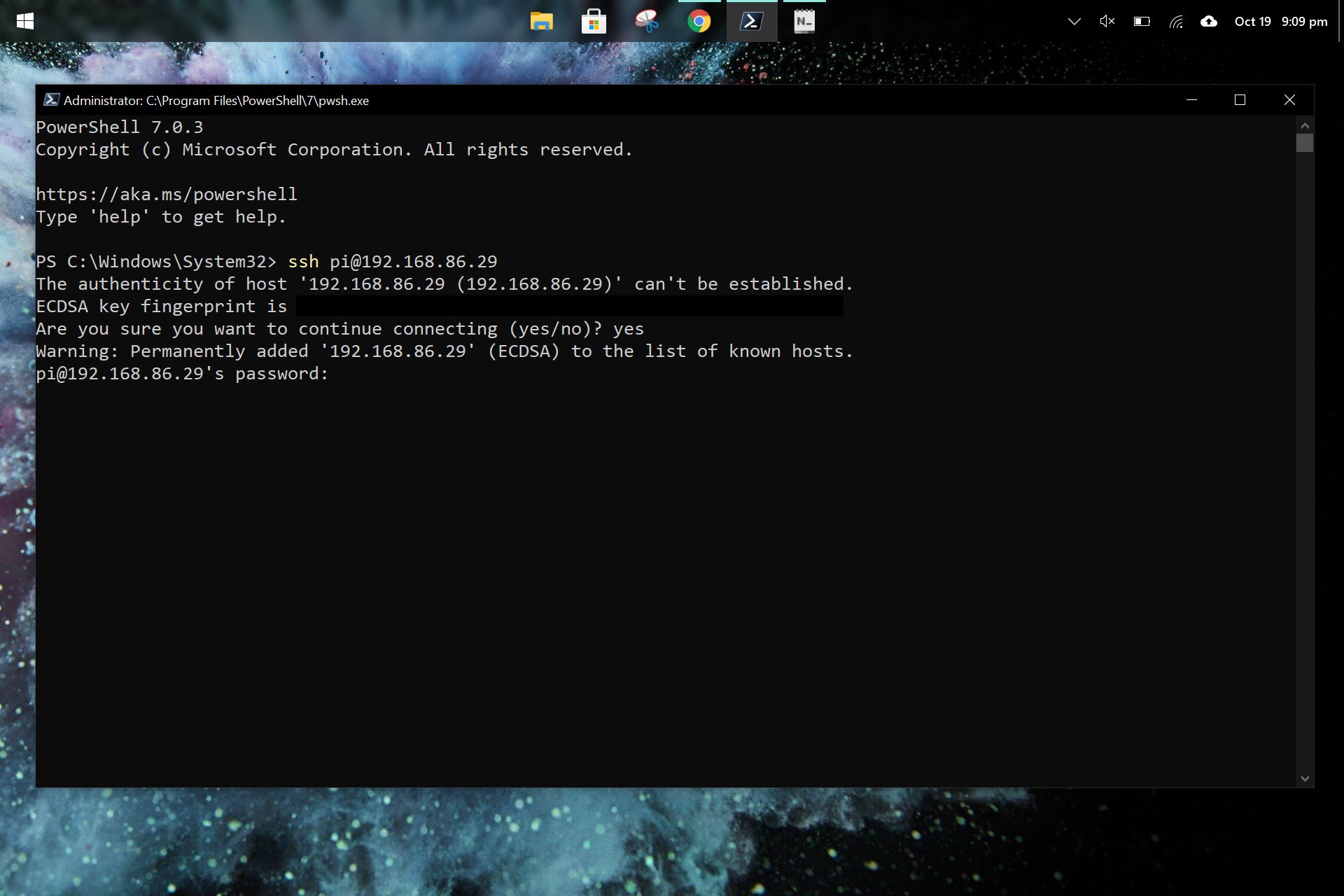
Step 3: Test Local SSH Connection
- Open a terminal or command prompt on your Windows machine.
- Type
ssh pi@and press Enter. - Enter the default password (
raspberry) or the one you’ve set.
Once you’ve confirmed SSH works locally, you’re ready to tackle the firewall challenge.
Troubleshooting Common SSH Issues
Encountering issues while setting up SSH? Don’t panic! Here are some common problems and their solutions:
- Error: Connection Refused: Double-check your Pi’s IP address and ensure SSH is enabled.
- Error: Permission Denied: Verify your username and password, and ensure your firewall isn’t blocking the connection.
- Error: Host Key Verification Failed: Delete the known_hosts file in your SSH directory and try reconnecting.
Now that your local setup is rock-solid, let’s explore how to access your Pi remotely.
Connecting to Raspberry Pi Behind Firewall Without MAC
When your Raspberry Pi is behind a firewall, things get a bit trickier. Firewalls are designed to block unauthorized access, which means you’ll need to configure port forwarding or use alternative methods to establish a connection.
Method 1: Port Forwarding
- Log into your router’s admin panel.
- Locate the port forwarding settings and create a new rule.
- Set the external port to 22 (default SSH port) and the internal IP address to your Pi’s address.
- Save the changes and test the connection using your public IP address.
Method 2: Using a Dynamic DNS Service
- Sign up for a free dynamic DNS service like No-IP or DuckDNS.
- Install the client software on your Pi to update the DNS record automatically.
- Use the assigned domain name to connect to your Pi instead of the IP address.
Method 3: Reverse SSH Tunneling
- Set up a server outside your network (e.g., on a cloud provider).
- Create a reverse SSH tunnel from your Pi to the external server.
- Connect to the external server and forward the connection to your Pi.
Each method has its pros and cons, so choose the one that best fits your needs and technical expertise.
Choosing the Best Method for Your Setup
Not sure which method to pick? Consider the following factors:
- Simplicity: Port forwarding is the easiest option if your router supports it.
- Reliability: Dynamic DNS is great for setups where your IP address changes frequently.
- Security: Reverse SSH tunneling offers an extra layer of protection but requires more setup.
No matter which method you choose, remember to prioritize security by using strong passwords and enabling two-factor authentication whenever possible.
Best Practices for Secure SSH Connections
Security should always be at the forefront of your mind when setting up SSH. Here are some best practices to keep your Raspberry Pi safe:
- Change the Default SSH Port: Switching from port 22 to a non-standard port can reduce brute-force attack attempts.
- Disable Password Authentication: Use SSH keys instead of passwords for added security.
- Limit User Access: Restrict SSH access to specific users or IP addresses.
- Keep Software Updated: Regularly update your Pi’s operating system and SSH software to patch vulnerabilities.
By following these guidelines, you’ll significantly reduce the risk of unauthorized access to your Pi.
How to Generate and Use SSH Keys
SSH keys provide a secure alternative to passwords. Here’s how to generate and use them:
- Open a terminal or command prompt and type
ssh-keygen. - Follow the prompts to create a new key pair (public and private).
- Copy the public key to your Pi by running
ssh-copy-id pi@. - Test the connection using your private key instead of a password.
SSH keys not only enhance security but also streamline the login process by eliminating the need to enter a password every time.
Advanced Techniques for Remote Access
Once you’ve mastered the basics, you can explore advanced techniques to further enhance your SSH experience. Here are a few ideas:
Method 1: Automating SSH Connections
- Create a script to automate the SSH connection process.
- Use tools like Cron to schedule regular connections or updates.
Method 2: Setting Up a VPN
- Install a VPN server on your network to create a secure tunnel for all devices.
- Connect your Pi to the VPN and access it as if it were on the same local network.
Method 3: Using SSH Jump Hosts
- Set up an intermediate server as a jump host for your SSH connections.
- Connect to the jump host first, then forward the connection to your Pi.
These advanced techniques can help you overcome even the toughest networking challenges.
When to Use Advanced Techniques
Advanced techniques are ideal for:
- Complex Networks: If your network setup is intricate, using a jump host or VPN can simplify management.
- High-Security Environments: For projects requiring maximum security, SSH keys and automated scripts are essential.
- Remote Monitoring: Automating connections allows you to monitor your Pi’s status without manual intervention.
While these methods require more effort upfront, they pay off in the long run with improved efficiency and security.
Troubleshooting Common Firewall Issues
Firewalls can sometimes cause headaches when trying to SSH into your Raspberry Pi. Here’s how to troubleshoot common issues:
- Error: Connection Timed Out: Ensure your router’s firewall isn’t blocking the SSH port.
- Error: Host Unreachable: Verify your Pi’s IP address and check for any network configuration issues.
- Error: Permission Denied (publickey): Confirm your SSH keys are correctly set up and permissions are properly configured.
If you’re still stuck, try resetting your router or consulting its user manual for additional guidance.
When to Seek Professional Help
While most issues can be resolved with some troubleshooting, there are times when seeking professional help is the best option:
- Complex Network Configurations: If your network setup involves multiple firewalls or advanced routing, a network administrator can provide valuable assistance.
- Security Audits: For high-security environments, hiring a cybersecurity expert ensures your setup meets industry standards.
Don’t hesitate to reach out for help if you’re unsure about any aspect of your setup. It’s always better to be safe than sorry!
Conclusion: Mastering SSH to Raspberry Pi Behind Firewall Without MAC
In this guide, we’ve explored everything you need to know about SSH to Raspberry Pi behind firewall without MAC Windows. From setting up SSH and configuring firewalls to advanced techniques and best practices, you now have the tools to remotely access your Pi with confidence.
Remember, the key to success lies in understanding your network environment and choosing the right method for your specific needs. Whether you opt for port forwarding, dynamic DNS, or reverse SSH tunneling, prioritizing security and efficiency will ensure your projects run smoothly.
So what are you waiting for? Grab your Raspberry Pi, fire up your favorite tools, and start exploring the limitless possibilities of remote access. And don’t forget to share your experiences in the comments below—we’d love to hear how you’ve used SSH to enhance your projects!
Table of Contents
- Understanding SSH and Its Importance
- Setting Up SSH on Raspberry Pi
- Connecting to Raspberry Pi Behind Firewall
- Best Practices for Secure SSH Connections
- Advanced Techniques for Remote Access
- Troubleshooting Common Firewall Issues
- Conclusion


Detail Author:
- Name : Miss Lupe Cormier
- Username : tremblay.myrtie
- Email : leann65@connelly.com
- Birthdate : 2007-05-13
- Address : 463 King Square Suite 208 East Celine, MN 17502
- Phone : 1-419-215-2131
- Company : Zulauf PLC
- Job : Legal Secretary
- Bio : Accusantium eligendi eligendi et totam molestiae. Delectus minima quis aspernatur placeat repudiandae. Molestiae omnis voluptas earum nesciunt nobis quam ut qui.
Socials
linkedin:
- url : https://linkedin.com/in/trinity_official
- username : trinity_official
- bio : Alias perspiciatis consectetur non qui quasi.
- followers : 2317
- following : 511
facebook:
- url : https://facebook.com/trinity_schuster
- username : trinity_schuster
- bio : Est nam et ratione vel ipsa quia. Aliquid odio quo libero facilis.
- followers : 1131
- following : 2347
tiktok:
- url : https://tiktok.com/@tschuster
- username : tschuster
- bio : Voluptas consequatur numquam voluptatum officia aliquam quibusdam sed.
- followers : 3593
- following : 2345